Articles > Book Summary - Blockchain and Distributed Ledgers
Date: 8th of October 2022.
This article was also published on Medium.
Book Details:
- Author: Alexander Lipton and Adrien Treccani
- Originally Published: 2021
- Genre: Blockchain and Cryptocurrency
- Pages: 480
Alexander Lipton is a professor, quant, and author with interest in a wide range of subjects including mathematics, physics, financial engineering, and blockchain technology. In Blockchain and Distributed Ledgers, Lipton provides an overview of the fundamental ideas and technologies pertaining to distributed ledgers.
Current Financial System
Banking institutions play the critical role of record keepers of money. Money is an obligation of private banks, while cash is an obligation of central banks. Money is created through lending whereby a borrowing event creates two entries in a bank's books — a deposit for the borrower's assets and a liability for the borrower corresponding to the bank's assets, thus money was created out of thin air.
When a loan is repaid, the record-keeping entries are reversed and money is destroyed. However, in case of borrower's default, the bank is unable to destroy the money and a forgery event occurs whereby the created money remains permanently in the system.
While the quantity of money increases steadily, its velocity is currently decreasing implying lower efficiency. The velocity of money is the frequency at which money exchanges hands; higher velocity implies higher economic activity.
In fractional reserve banking, banks borrow and lend to each other to maintain their reserve requirements. During times of financial crisis, defaults can propagate across the system making the system unstable. In addition, the system depends on numerous intermediaries and has become too complex to be understood by its own players. Expensive legacy IT systems are used to prove compliance with capital requirements, resulting in banking activities concentrating with the players who can afford the regulatory burden.
Domestic payment and settlement systems also involve multiple intermediaries each charging their own fees. Credit card payment origination, clearance, and settlement are especially costly. Cross-border payments include even more intermediaries in addition to foreign exchange slippage, making them costlier and slower.
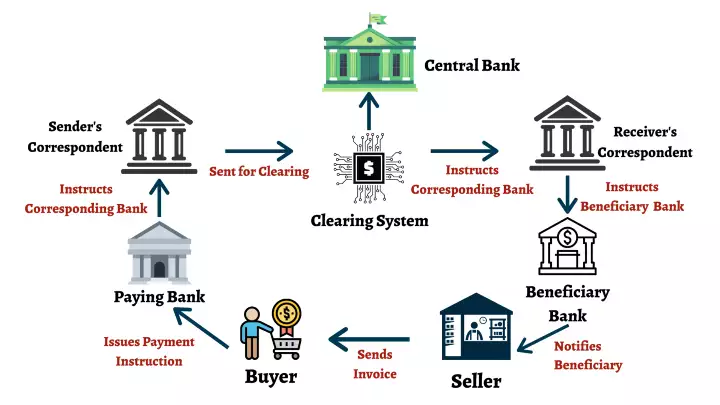
The global financial crisis of 2008 was a missed opportunity to overhaul the financial system. Instead, it made the system more centralized and interconnected by moving the clearing of OTC derivatives to specialized clearing houses. Further, central banks engaged in massive quantitative easing pushing interest rates to record lows, resulting in frustration with monetary policy.
Distributed Ledgers
The complexity of the existing banking system arises due to the commingling of record keeping and transaction execution. Separating these activities will make banking more agile. Distributed Ledgers can be used to vastly improve the speed of transaction execution and record keeping.
Distributed ledgers are accounting databases maintained by multiple parties over a peer-to-peer network, in contrast to the client-server paradigm which relies on centralized endpoints acting as intermediaries between peers. Ledgers can be permissionless allowing anyone to participate, or permissioned allowing only authorized parties to view and participate.
Blockchains are shared distributed ledgers consisting of a chain of data blocks where each block contains a batch of transactions. The integrity of the blockchain is maintained using a hash function where each subsequent block stores the hash of its previous block.
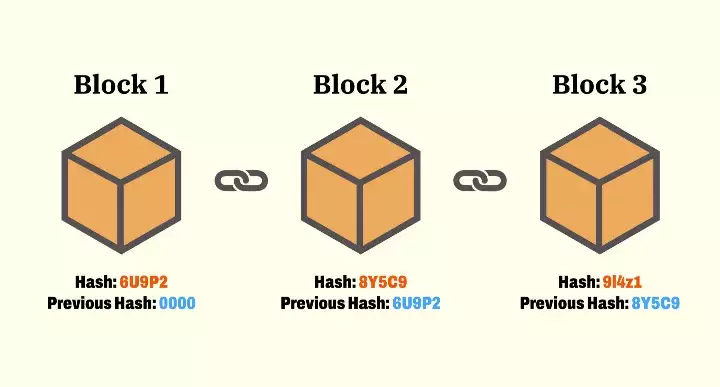
Two possible attacks on the integrity of a distributed ledger are double spend and Sybil attacks. Double spend attacks occur when the network is split between two different but incompatible transactions, while Sybil attacks occur due to the anonymous nature of blockchains whereby an adversary can create multiple pseudonymous identities and use them to manipulate voting on the network.
Double spend and sybil attacks are mitigated by introducing a consensus algorithm. One such consensus algorithm is Proof-of-Work (PoW) which dictates that only blocks with a valid resolution to the prohibitively expensive hash problem (work) are accepted by the network. Verifying the work is trivial and deterministic. Miners who solve the problem are rewarded with freshly minted coins as well as all the transaction fees in the block.
A fork occurs when two blocks are mined at the same time. BTC's policy is to accept the longest chain as defined by the one with the longest cumulative work done. This policy, called the consensus chain, is susceptible to the 51% attack whereby an attacker controlling more than 50% of the network's hashing power can dictate what the longest chain should be. It is hence advisable to wait a few blocks before considering a transaction final.
Proof-of-Stake (PoS) is an alternative consensus algorithm to PoW whereby participants are allowed to vote on the next valid block by staking a set amount of coins as collateral. Malicious attackers have their stake slashed, and to prevent Sybil attacks, the voting influence is proportional to the amount of coins staked.
Cryptography
Symmetric key cryptography is the traditional approach to cryptography whereby the secret key used to encrypt / decrypt cipher text is shared amongst the participants. Per Kerchkoffs principle, such a scheme is secure when it can't be broken despite everything about it (except the secret key) being publicly known.
One such scheme is Caesar's cipher whereby each plaintext character maps to a cipher equivalent. Caesar's cipher is susceptible to brute-force attacks and frequency analysis. Vigenère cipher is an improvement that uses a stream of key letters such that the position of the character in combination with the corresponding key value is used to encrypt that character. Key is repeated if the message is shorter than the key.
The only secure symmetric key cipher is the One-time Pad (OTP) which generates a Vigenère sequence using a random key that is as long as the message. To avoid having to store a key as large as the message, a pseudo-random generator and a seed are used to produce a stream of keys, this is known as stream cipher.
Asymmetric Key Cryptography
Asymmetric key cryptography is the modern approach whereby two keys are used for encryption instead of one. A public key which one can use to encrypt messages that can only be decrypted by the corresponding private key. In addition, the public key can be used to verify that a particular message was signed by the corresponding private key.
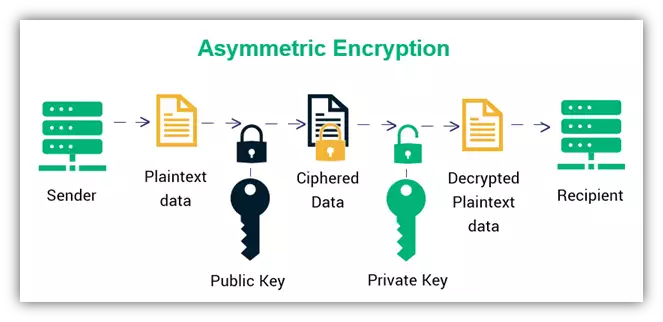
The key idea behind asymmetric key cryptography is the use of trapdoor functions which are difficult to solve unless prior information is known. RSA algorithm relies on Euler's theorem to produce trapdoor functions such as the exponent modulo, El-Gammal's algorithm is more modern and uses discrete logs, Elliptic curve digital signature algorithms (ECDSA) are the most advanced and use elliptic curves as trapdoor functions. Bitcoin and other popular protocols use the secp256k1 elliptic curve.
Hash Functions
Hash function are trapdoor functions that are collision-free such that it is difficult to find two messages that have the same hash. Hash functions are considered puzzle-friendly if for a given pre-image it is infeasible to find the hash of that pre-image plus a salt faster than O(2^n) such that the image belongs to a specific output set. One hash function that satisfied both properties is the SHA-256 algorithm which is used by Bitcoin.
Hash functions that hash to a shorter output will have collisions due to the pigeonhole principle. The Pigeonhole principle can be applied to the birthday paradox which counterintuitively shows that the probability of two people sharing the same birthday from a set of N people is just 50% when N is 23, and almost 99.9% when N is 70. In the context of cryptographic signatures, this implies that one can find two pre-images that map to the same hash, especially when the pre-images are a low number of bits.
SHA-256 uses the Merkle-Damgård transform to pad messages by adding zeroes ensuring that the length of the message is a multiple of 516 bits. However, algorithms such as MD5, SHA-1, and SHA-2 are susceptible to the length-extension attack which allows an attacker to calculate the hash of the concatenation of an original message plus an additional one. Bitcoin hashes a message twice to mitigate the above. The newer SHA-3 algorithm is resistant to such an attack.
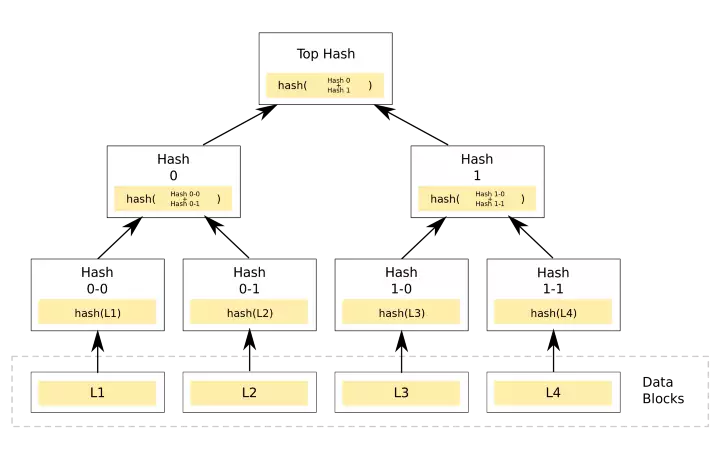
Hash functions are also used in the merkle tree data structures consisting of the transactions in a block, where the leafs represent wallets / accounts. Merkle trees are tamper-proof and as such ensure that a change along the path of the root will change the hash of the root itself. Using merkle trees, one can also verify that a particular transaction exists in the tree. The hash of the merkle tree's root is used as the hash pointer when chaining blocks of data together creating an immutable tamper-proof blockchain.
Wallets
Wallets are direct mappings from public key to private key. A wallet requires four key components:
- Network node: track state of blockchain while maintaining a local copy. It also acts as a rely for broadcasting transactions, and exposes an API for querying blockchain primitives.
- Indexers: restructure data from nodes to build easily queryable datasets, maintaining a consolidated view of transactions and balances.
- Wallet app: liaise between wallet owner, keystore, and indexer. Facilitate transaction approval, recommend fees, and affirm transaction confirmation.
- Keystores: secure secret key persistence, may be a local file or database with additional protections such as encryption.
Most cryptocurrencies use 256-bit keys which allow for 10^77 possible combinations, making it impossible for new secret keys to collide with existing ones. To ensure true randomness, wallets employ secure Pseudo Random Number Generators (PRNG) which are computationally indistinguishable from true randomness.
Hierarchical deterministic wallets generate unlimited number of random secret keys from a single secret seed. The seed phrase can be derived from a mnemonic code as per BIP39 which uses dictionary words where the first four letters can unambiguously identify a complete word.
Key derivations can be hardened or non-hardened. Hardened requires the parent secret key to generate any child key. Non-hardened don't require the hardened secret key but guarantee any derived child key can be calculated from parent key.
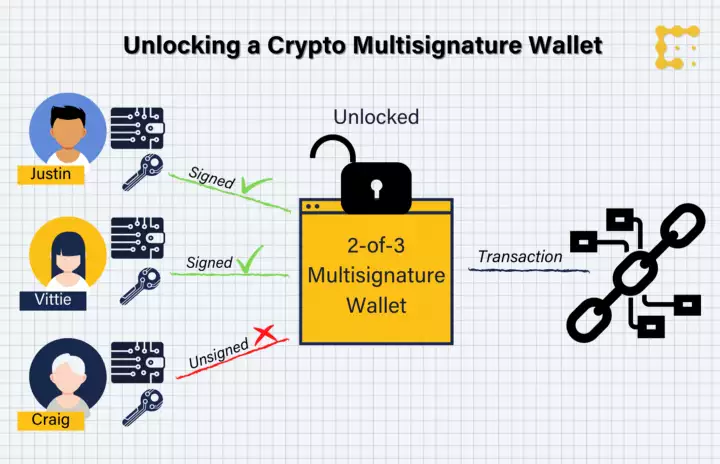
Multi-signature (multi-sig) transaction approvals is a safety mechanism which requires multiple parties to sign a transaction before approval. Validation can be off-chain, or on-chain as supported natively by Bitcoin, and by Ethereum via smart contracts.
Bitcoin
Bitcoin is a transaction-based ledger where transactions are organized in chains going back to the coinbase transactions or the genesis block, a transaction feeds into the next. A transaction can have multiple senders / receivers, and its id (TXID) is 32 bytes long and is generated by hashing it twice then bit reversing. The Bitcoin protocol can be though of as a vehicle for performing transitions in a Markov chain.
Participants in the Bitcoin protocol can either run a Full node which stores a local copy of the full ledger history, or a Simplified Payment Verification (SPV) node which stores only the headers to the longest chain.
Bitcoin operates using a LIFO stack based scripting language with operations such as Pay to PubKey (P2PK), Pay to PubKey Hash (P2PKH), and Pay to Script Hash (P2SH). P2SH can be used to code very complicated scripts.
Executed transactions are sent to the memory pool where they await inclusion in a miner's block. When miner's mine a new block, a Coinbase transaction with no sender is generated containing the miner's BTC mining reward.
Bitcoin's mining process involves searching for two nonces, one in the block header and te other in the Coinbase transaction, such that the hash of the block is lower than a pre-defined difficulty target. The difficulty adjusts every 2016 blocks based on the network's hashing power, thus it can't be compared to gold where the closure of a gold mine doesn't affect the cost extraction for other mines.
Bitcoin's PoW consensus algorithm halves the mining reward every four years. Mining time is random and follows an exponential distribution with an average of 10 minutes, with each block on average containing 2,000 transactions occupying 1MB of storage.
Bitcoin uses the ECDSA algorithm for signing messages, the secret key is 256 bits, public key is 512 bits, messages are 256 bits, and signatures are 512 bits. Bitcoin uses the Wallet Export Format (WEF) to encode the ECDSA keys and make it easier to copy around.
Bitcoin's returns are best represented by a Generalized Hyperbolic distribution as per experiments by the book's author. Bitcoin can be valued by using the stock-to-flow valuation model. And its dominance can be modeled using mathematical epidemiology models such as Susceptible-Infected-Removed (SIR).
Ethereum
Ethereum is a protocol with an account-based ledger and a distributed computing platform that went live on July 30th 2015 with a genesis supply of 72,010,000 pre-mined ETH tokens. Ethereum is capable of storing and executing arbitrary code on the Ethereum Virtual Machine (EVM) in the form of smart contracts. Ethereum addresses can be either Externally Owned Accounts (EOA) or Smart Contracts (SC). Only EOA have private keys.
The EVM is a sandboxed environment running on every Ethereum node where every node executes all the computations going through the network. Computations are paid for using ETH tokens based on a pay per operation model, with each opcode in the EVM having a pre-defined cost. This is to prevent denial of service attacks. Transactions declare two parameters, STARTGAS which is the maximum amount of gas the sender is willing to pay, and GASPRICE which is the amount of eth per computation unit. Total block gas limit is around 100 million gas.

Due to Ethereum's fast block mining, orphan blocks called uncles are created. Uncle blocks are rewarded as it increases the network's security by incentivizing extra work even if it doesn't contribute to te longest chain.
Smart Contracts
Smart Contracts contain deterministic computer commands that don't require an intermediary and are reliably executed by all miners. SCs run on-chain within the EVM and require the use of other smart contracts called Oracles to access oof-chain data. The most popular oracle provider is the partially decentralized reputation-based oracle network ChainLink.
Smart Contracts can be used as external ledgers for creating new pre-mined tokens. The most popular standard is ERC-20 which is used for managing fungible tokens. It requires the smart contract to implement six functions: totalSupply(), balanceOf(), transfer(), transferFrom(), approve(), and allowance(). ERC-20 tokens are sometimes issued as part of an Initial Coin Offering (ICO). Non-fungible tokens (NFTs) are smart contracts tokens that follow the ERC-721 standard.
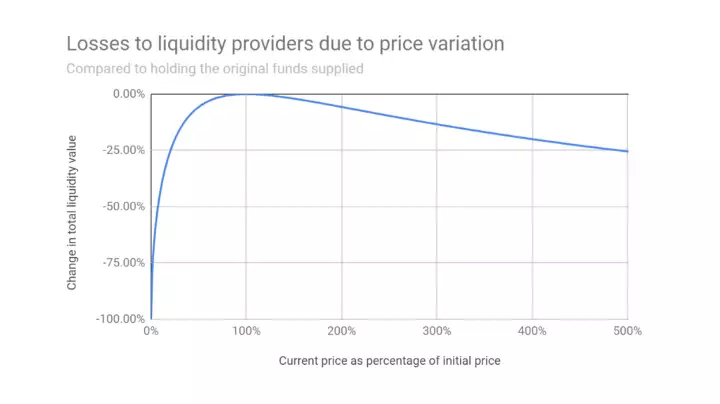
Another use of smart contracts is automated market makers. AMMs facilitate the exchange of tokens through the use of tokens staked in pools. Several types of AMMs exist such as constant sum, constant product, and mixed. Impermanent loss occurs when the market maker's stake changes value as the price of the tokens in the pool change. IL is highest for constant sum AMMs, followed by mixed rule, with constant product experiencing the smallest IL.
The most ambitious use for smart contracts is the creation of Decentralized Autonomous Organizations (DAOs), which are self-governing organizations where members vote amongst themselves and interactions are stored on-chain.
Central Bank Digital Currencies / Stablecoins
Central Bank Digital Currencies (CBDCs) are government-sponsored stable cryptocurrencies and can be of two types: wholesale used for value circulation amongst financial institutions, and retail used for value exchange by the whole population.
Benefits of CBDCs over cash is a reduction in crime and a digital economy more accessible to the unbanked. However, it makes it easier for banks to enforce negative interest rates which have been showed to be ineffective for spurring economic activity.
CBDCs require KYC and AML which aren't the specialty of central banks. Thus, CBDCs are better issued by banks such as Narrow banks whose only assets are central bank cash and short-term government obligations. Narrow banks' assets exceed their deposit base and tend to refrain from issuing lends except when fully collateralised by the borrower's assets.
Stablecoins
The private version CBDCs are called stablecoins. Stablecoins aim to mitigate the volatility of cryptocurrencies by pegging the price of the stablecoin. There are six types:
- Fully collateralised by individual fiat currencies.
- Fully collateralised by baskets of fiat currencies.
- Partially collateralised by fiat.
- Over-collateralised with crypto.
- Algorithmically stabilized.
- Asset-backed (commercial paper, Tbills, etc..)
Stablecoins over-collateralised with other coins are susceptible to black swan events due to the volatility of the underlying coins. They also suffer from negative feedback loops where the selling of the underlying collateral causes the price of the stablecoin to fall even faster.
It isn't currently possible to build a decentralized stablecoin because pegging the price to an off-chain fiat currency requires oracles which are prone to manipulation. For stablecoins to be considered sound money, they need to have these six requirements per Copernicus:
- It must not change value expect by government deliberation.
- A single place for minting.
- When new currency is issued, old currency must be demonetized.
- Unchangeable rules to mint.
- Must not issue too much.
- All coins issued at the same time.
Stablecoins are a better solution for modern commerce compared to fiat currencies as fiat currencies suffer from high handling and exchange costs. In addition, the reserve status of the fiat USD causes trade imbalances and exacerbates international frictions. Creating an independent international reserve currency backed by real world assets such as the Digital Trade Coin (DTC) will make the global monetary system more stable in the long run.
Innovations and Use-cases
The three current research topics are blockchain interoperability / intraoperability, privacy, and scalability.
Intraoperability is the ability to exchange different assets defined on the same blockchain, while interoperability is the ability to move assets between different blockchains. The former can be achieved through the use of AMMs, while the latter through te standardization of asset definitions, or at the mechanical protocol level.
Privacy
Privacy can be achieved in three different ways: payment channels, coin mixing, and cryptographic obfuscation.
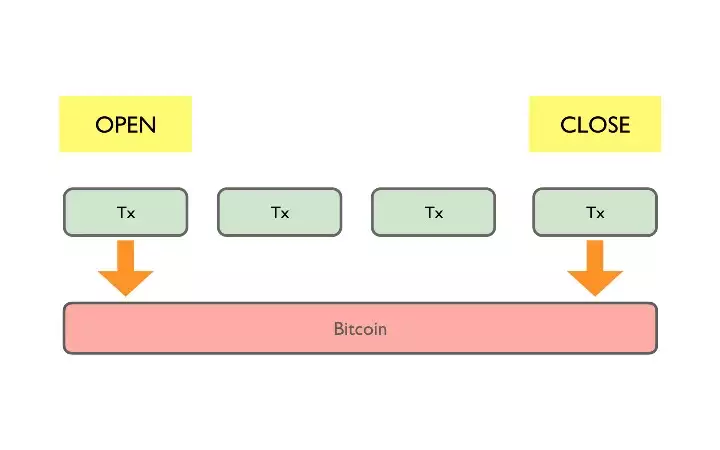
Payment channels are private off-chain channels created by two agents and seeded with an initial deposit from each. The final net value of the transfer is recorded as a transaction on-chain once the payment channel is closed.
Coin mixers allow agents to mix their coins with other agents while choosing a different address as the destination after mixing. Coin mixers can be both centralized or decentralized.
The final approach is to privacy is cryptographic obfuscation using zero-knowledge proofs (ZKPs), whereby an agent can prove they know a secret to a verifier without revealing the secret. ZKPs have to fulfill three criteria:
- Completeness: prover can convince verifier she knows a secret.
- Soundness: prover can't convince verifier of a secret she doesn't know.
- Zero-knowledge: secret information doesn't leak as part of the process.
Zerocash (Zcash) is a privacy-first blockchain that is an extension of Bitcoin. It uses Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk-SNARKS) which is a more efficient approach to proof construction.
Scalability
The third and final innovation is scalability. The scalability trilemma claims that blockchains can only have two of three properties: decentralization, scalability, and security. Scalability can be solved by using Layer0 protocols, Layer1 protocols such as Proof-of-Stake (PoS), Proof-of-Capacity (PoC), Byzantine Fault Tolerance (BFT), and DAGs for security and transaction sharding, and Layer2 protocols for fast transaction processing and payment channels.
Future Use-cases
DLT have a multitude of future use-cases, these include Identity and Access Management (IAM) systems, voting, and electronic health records for governments. Chain management and trade finance for supply chain industry. Audit, programmable money, and trade clearing and settlement for the finance industry.
DLTs can be used to make auditing continuous, comprehensive, transparent, and immutable (reduce fraud). Programmable money is when restrictions are placed on the usage of money, it can be used for humanitarian aid or fighting climate change. And finally, the time it takes to clear and settle trades can be reduces from its current 2-3 days to mere hours or minutes.
Tokenization of real world assets is also another frontier for DLT innovation where the purchasing, renting, and maintenance of real estate can be made more transparent and significantly faster.
